Best SMS OTP Service Providers in India
In a world where everything is becoming digital-first, it is crucial to authenticate users and verify customers with ease...
Learn more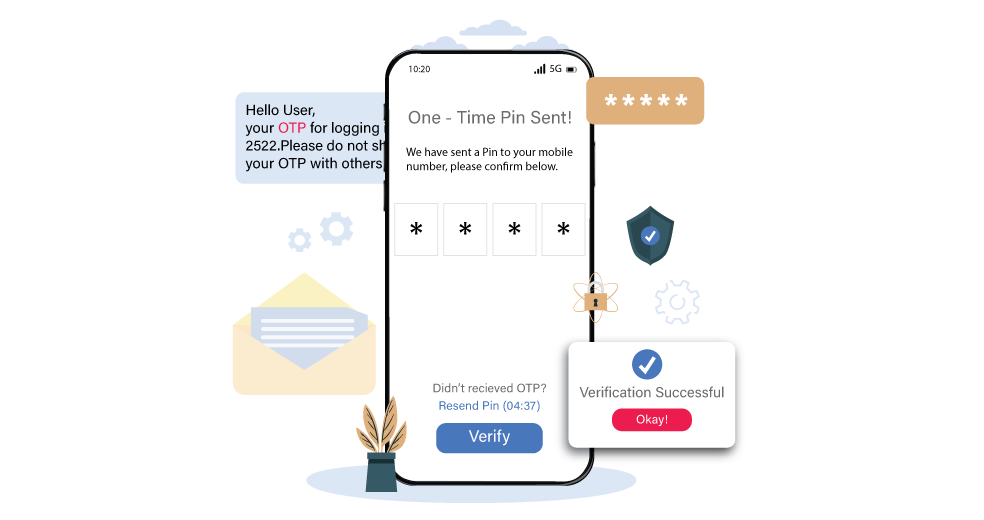

A One-Time PIN code, or OTP code for short, is a temporary, single-use number that a system delivers to a user to confirm their identity or give them permission to complete a transaction. Unlike ordinary passwords, which are good for a long time, OTPs are only good for a limited time (usually a few minutes) or until they are used. This makes them safer against many common cyber dangers.
A one-time PIN or password (OTP) is an extra layer of protection that makes sure the person doing something is truly the authorized user. Here's a step-by-step overview of how OTP verification works:
1. User Initiates ActionThe procedure begins when a user seeks to perform a sensitive action, such as entering into their account, making an online purchase, transferring money, or resetting a password. Because these actions include personal or financial information, the system adds an extra step to verify the user's identification.
2. OTP generationWhen the system recognizes the request, it generates a unique, random number or alphanumeric code. The method used to generate this OTP may vary:
This randomization and uniqueness ensures that the OTP cannot be easily predicted or reused.
3. Delivery to UserThe OTP is delivered to the user via a secure communication channel after it has been generated. The following are the most popular delivery methods:
This guarantees that the OTP reaches a channel that has already been confirmed to be the user's.
4. User Enters the OTPThe user then enters the received OTP into the program, website, or form that requires verification. This phase ensures that the individual carrying out the action has access to the registered channel (phone, email, or app).
5. Validation of OTPThe system checks right away:
If the OTP is valid and correct, the system will proceed. If not, access is refused, and the process may have to restart.
6. Access Granted or Action CompletedWhen the OTP is successfully confirmed, the system takes the appropriate action, such as allowing login access, confirming the transaction, or resetting the password. If the OTP is wrong or expired, the request is denied, and the user may be required to get a new OTP.
There are several widely used methods to guarantee that OTPs remain both secure and user-friendly:
OTPs can be sent through various methods based on specific needs:
OTPs provide numerous benefits that enhance their security compared to traditional static passwords:
OTPs are frequently used in the following typical scenarios:
To maintain the security and usability of OTP systems, businesses should adhere to the following guidelines:
A One-Time PIN (OTP) code plays a crucial role in contemporary security by balancing usability and protection. OTPs are utilized for transaction confirmations, secure logins, and identity verification, protecting both businesses and users from fraud, unauthorized access, and credential theft.
When using strong generation methods, secure delivery channels, and appropriate expiry and validation processes, OTPs greatly enhance an organization’s security framework.
As an OTP SMS provider in India, Shree Tripada offers prompt, reliable, and secure OTP delivery, assisting businesses in improving user trust while upholding high security standards.
In a world where everything is becoming digital-first, it is crucial to authenticate users and verify customers with ease...
Learn more
Don’t like giving your real phone number to every app or website? You’re not alone! Many people now use special phone...
Learn more
You are signing up for a fun app or buying a toy online. Instead of waiting a long time for a message...
Learn more
You look at your phone and see a message: "Your OTP is 458392. Don’t share this code."...
Learn more
These days, we do a lot of things on our phones and computers, like playing games or talking to friends...
Learn more
OTP services are used in many places like banks, online games (to check if you're real), social media, payments...
Learn moreImportant Links
Shree Tripada Infomedia India Private Limited
Corporate Head Office:
706 , 7th Floor , North Plaza, Nr 4D Square mall, Beside PVR, Opp Palladium
Nr.Visat Circle ,Motera, Sabarmati, Ahmedabad, Gujarat 380005